Intro to Secrets Management using Vault
TL;DR Using short-lived secrets to access a database is much more secure than standard credentials
So Thursday (April 9th) I participated in an online blue team defense simulation event, known as OpenSOC.
TL;DR It was an amazing event, I am ever thankful for being able to apply knowledge.
What follows is:
According to their website found here: https://opensoc.io/
OpenSOC is a blue team defense simulation that is as close to “the real thing” as it gets. This isn’t just another CTF. We’ve built this platform to train real-world responders to handle real-world situations. Our environment is a highly portable, fully functional replication of an enterprise environment, complete with all the trimmings - Active Directory, Exchange, distributed networks, various sensors, log aggregation, end-user simulation, and more.
OpenSOC is comprised of over a dozen open source projects, including the below.
The tools they list are what you would think of:
+ others
 screenshot from the OpenSoc website.
screenshot from the OpenSoc website.
Twitter… Seriously twitter!
A post came across my feed asking for interested. I responded and apparently so did enough people that we had 700 people during the event.
Sign up was here:
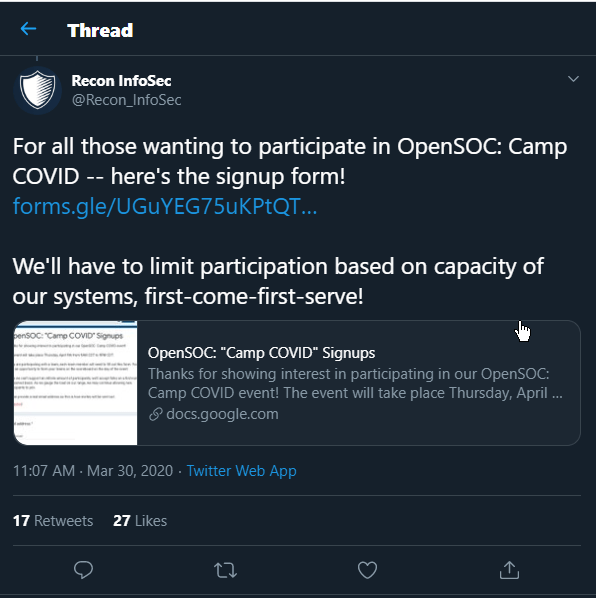
Twitter is great:
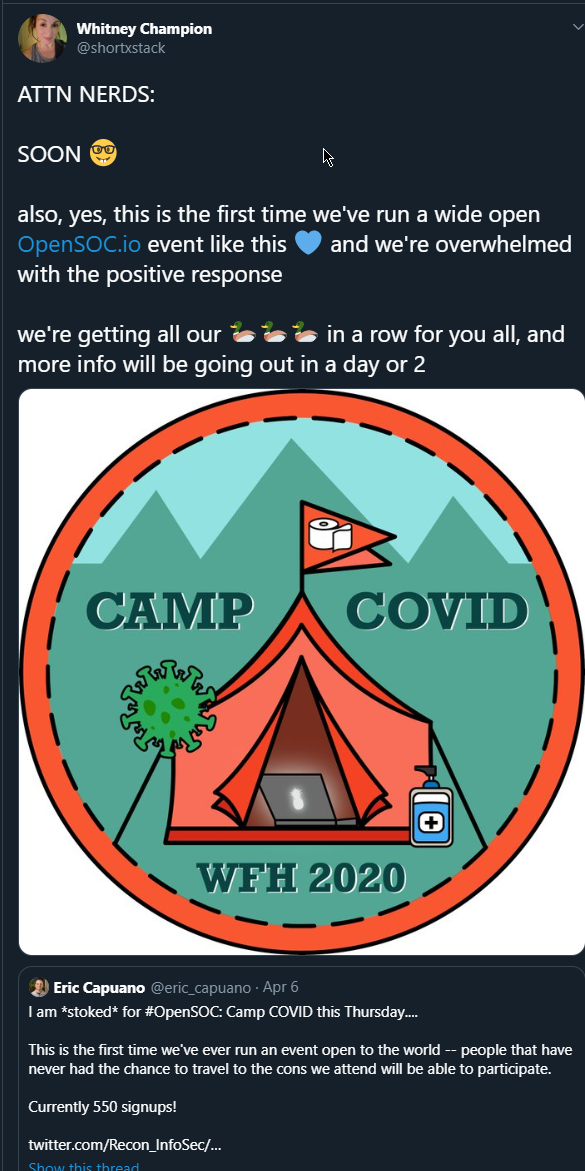
The event was not a live defense like a normal red team vs blue team event. It was a browser based blue team investigative CTF. It was amazing.
Being browser based made it much more accessible. Participants did not need a laptop that could handle a virtual machine, or RDP. They just needed something that could run a browser!
Sorry I did not get a screenshot of the Challenge page. But there were lots of challenges!
Again it was all browser based:
Graylog was used as the SIEM. Moloch was for full PCAP analysis OSquery for endpoint visibility
Please note, images have answers to challenges redacted (in-case they are reused)
You can see my setup in Graylog here. I added some fields to help with a challenge I was on at the time.
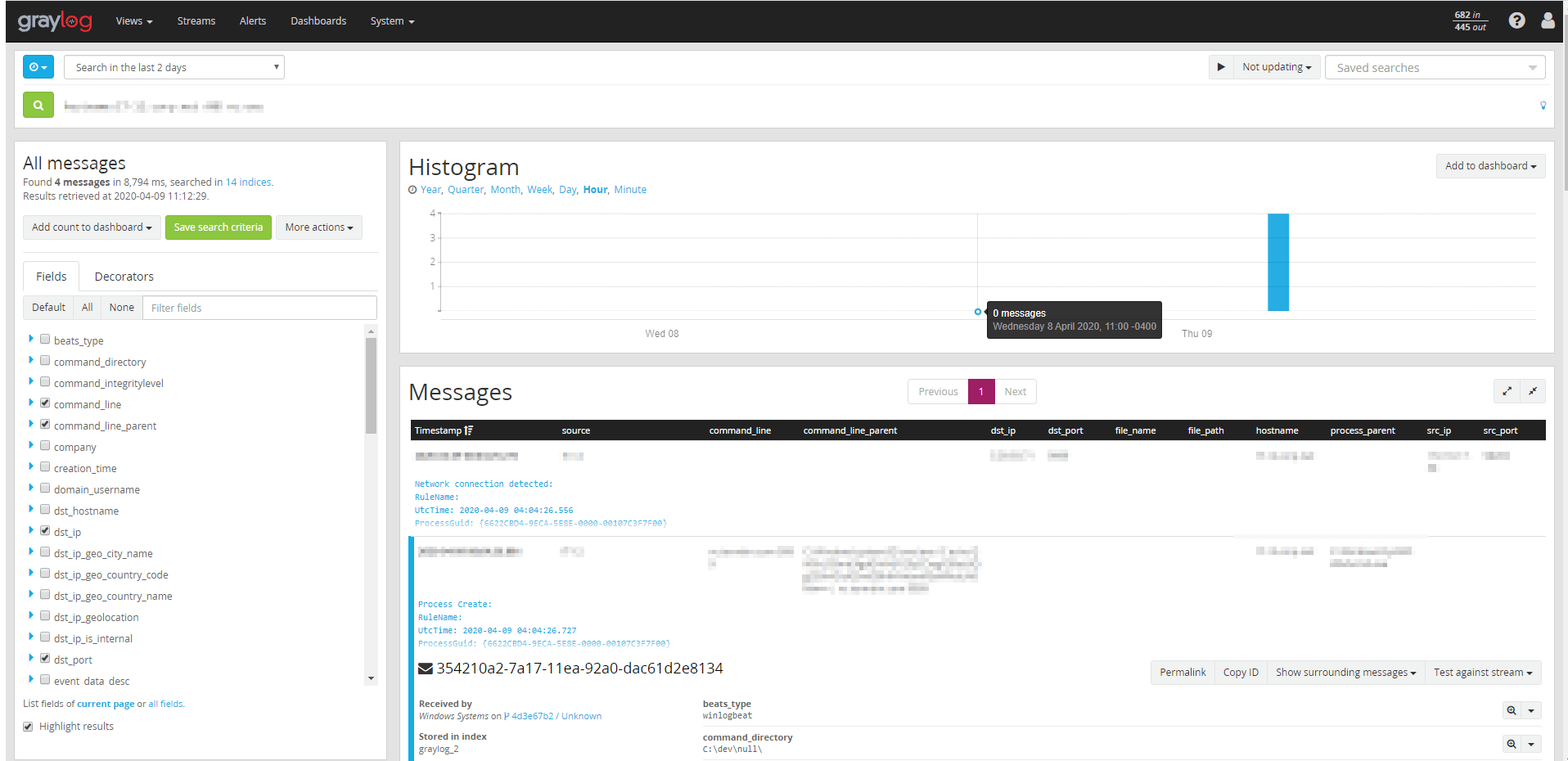
There was a GUI to run OSquery. I thought this was amazing because it makes it accessible to so many participants:
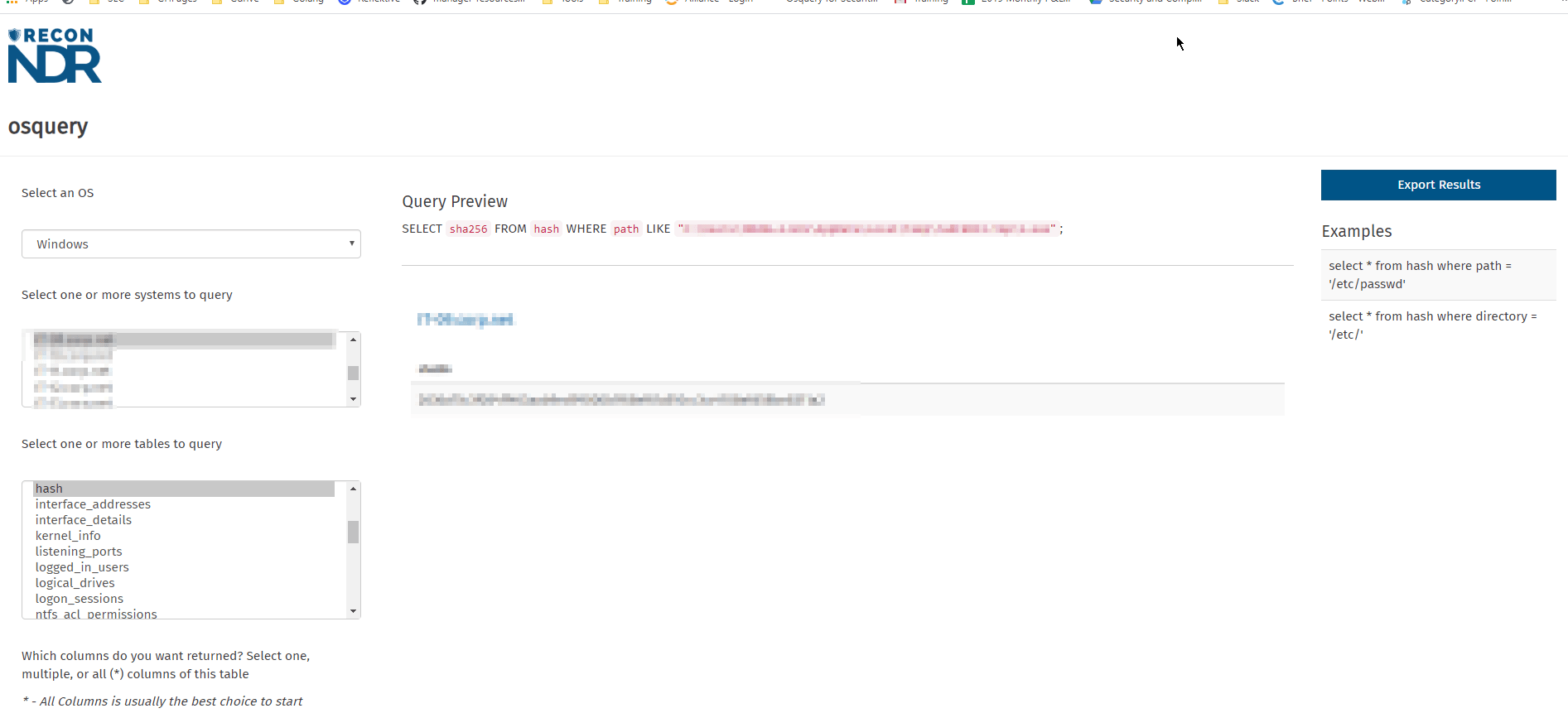
A big thank you to @shortxstack who created the GUI for it.
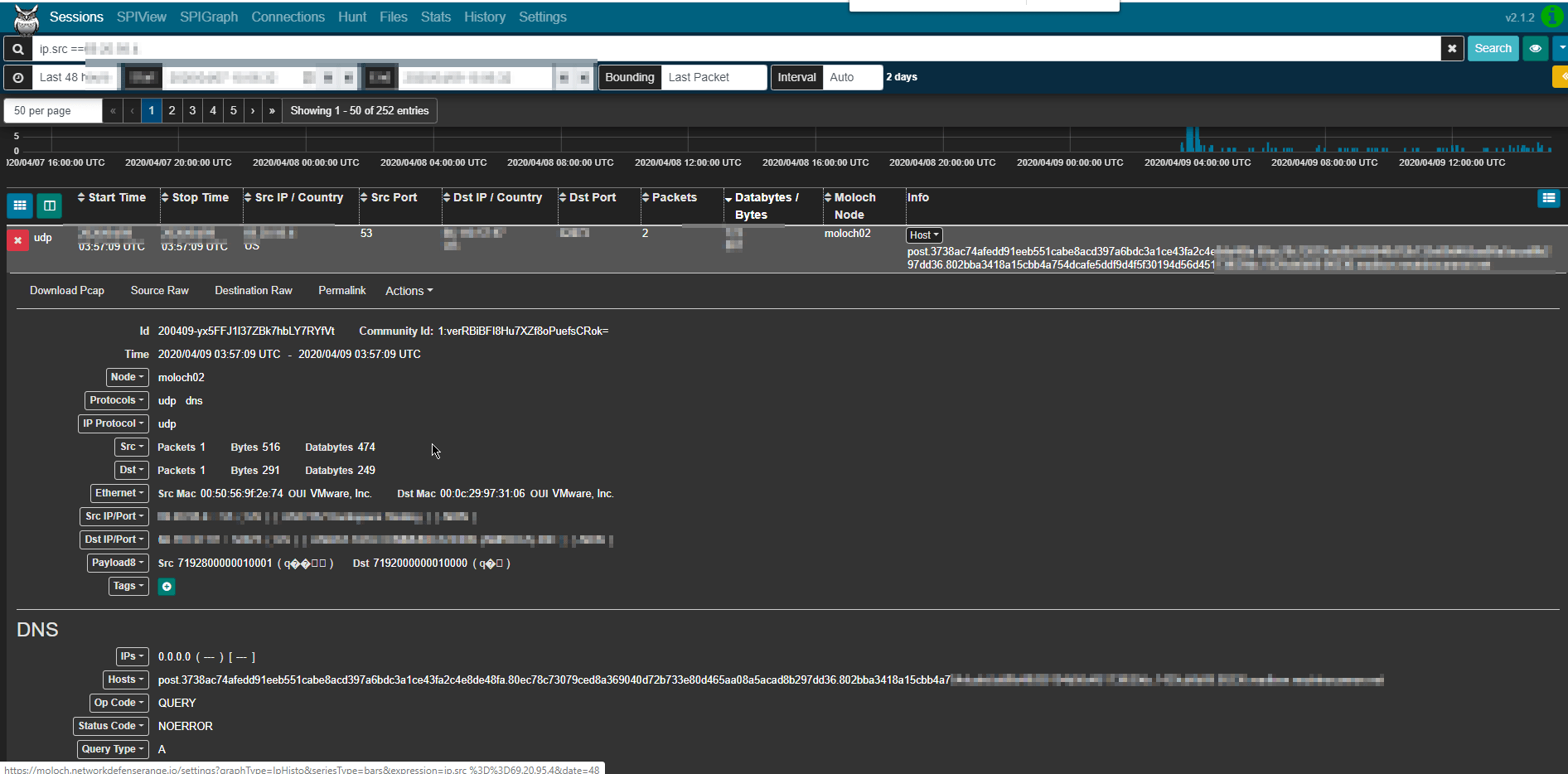
The opportunity to use Moloch was invaluable. The tool is amazing and opensource. It relies on full packet capture, which would not be an option nor practical for many organizations. Example screenshot below of the information you can glean:
The challenges varied and required different skill sets:
There were some memory analysis and Virtual Machines that could be downloaded as well.
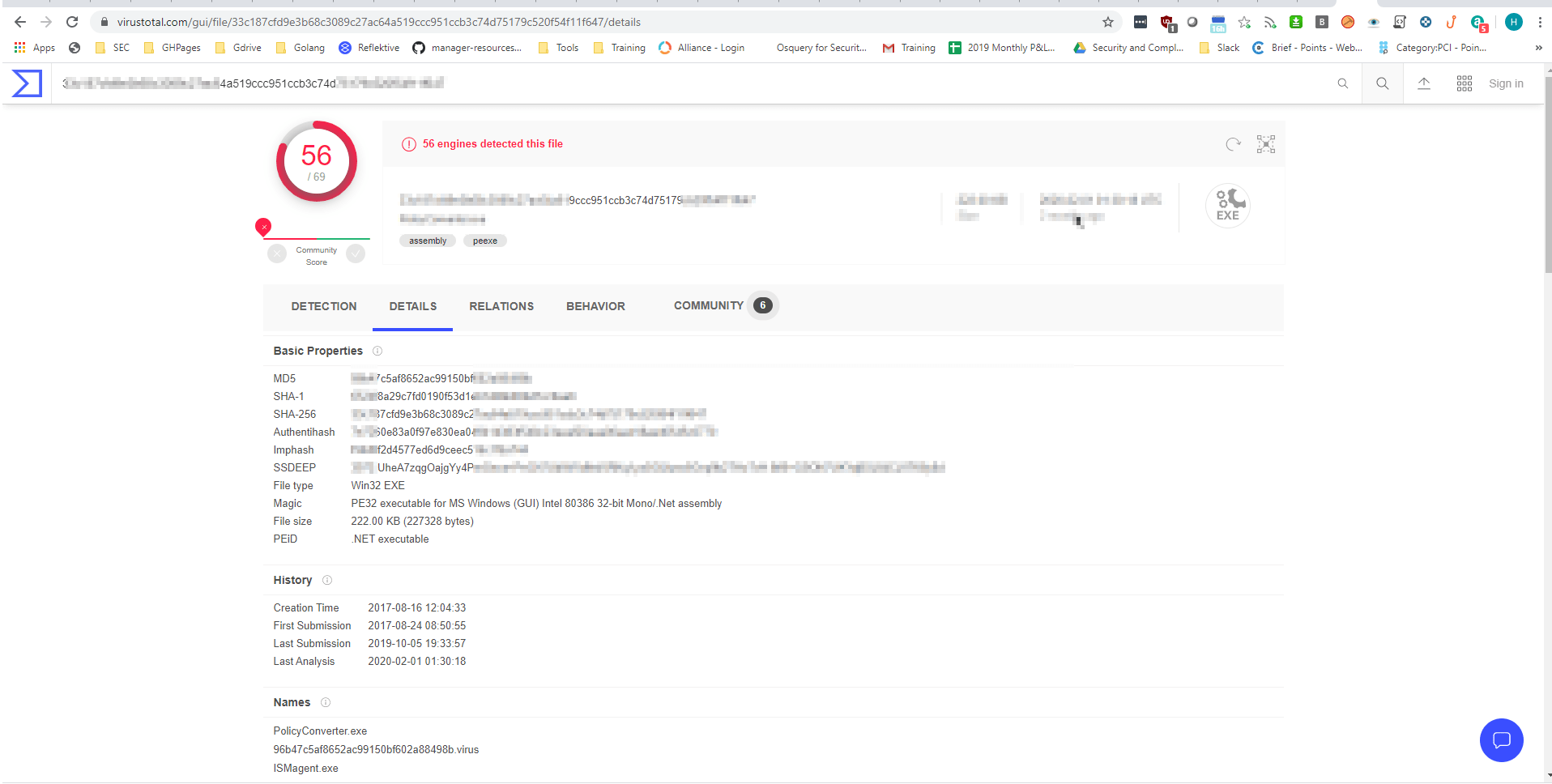
The challenges were not just WITHIN the 3 tools. An example was searching for hashes, using VirusTotal to solve, an example here:
I had once participated in ProsvJoes CTF at BsidesLV. As such I expected a hands on ‘defense’ event.
The 3 main tools to be used were Graylog, Moloch and OSquery. For my team, I focused on OSquery.
There is a great course from “Applied Network Defense” that I had started but never finished. So I quickly ran through the usage videos to get a handle on that. The course can be found here networkdefense.io/library/osquery-for-security-analysis.

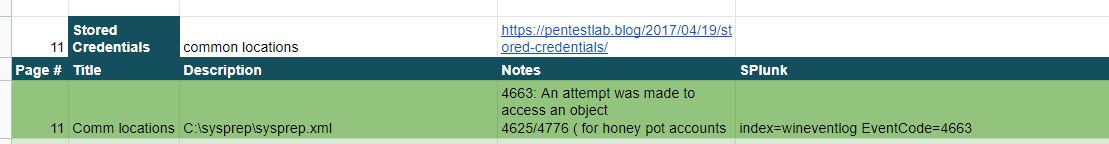
I had completed the eLearnSecurity Incident Responder certification exam in December (course found here: IHRP. So I had a large list of investigating queries to use. For my exam I had them in Splunk and ELK search formats)  .
.
So I thought it would be easy enough to convert them to Graylog. Or at least use as a reference sheet.
Well.. Not great, but also not bad! We finished 44th place out of 194 teams! Which personally is a great achievement.
Even though I had the day off work (thanks Boss!) it ended up being a busy day off the OpenSoc challenges. I was still fortunate to smash about 6-8 hours (give or take) in the event.
Our team consisted of Canadians:
Excited to say I ended up getting the most points for the team. In hacker/pentesting CTFs I am never #1, so this was a pleasant surprise. This was more due to the fact I could spend the most time on the event :).
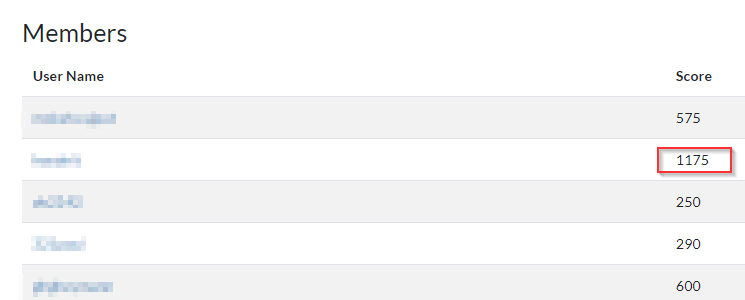
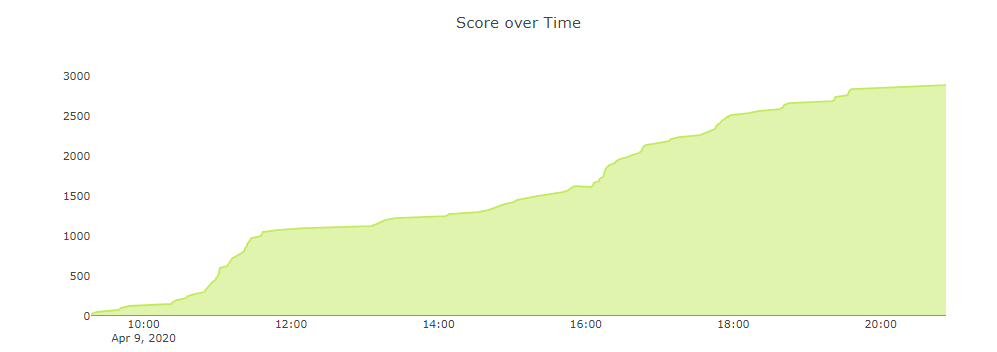
As other team members work slowed down, we were able to pick up more points:
In December, right before New Years I submitted my report for the eCIR exam. It was 2 days of investigation within Splunk and ELK, with the goal of identify how bad a theoretical companies network had been owned.
Also thanks to my amazing workplace (current as of 14th Mar 2020) for the funding to do the course and exam! If you want to check them out, great workplace: Check here work
With 2 different scenarios, with a child and parent domain it was quite intense and difficult. They had a PCAP supplied with one scenario that you could analyze in conjunction with the logs.
I passed the exam and found it valuable and ‘moved on’ focusing on my next learning goal. What surprised me is how applicable the learning from the course and exam was to OpenSoc. Even though it wasn’t the exact same tools, the investigate process was very similar.
Understanding what the logs would give you, what information you needed, what to look at after you found an IOC, where to pivot etc. These were all transferable skills. So after OpenSoc, I have a new appreciation for the actual skills learned from the course.
If you want to check the course out, you can find it here
And to finish off this part. Here is my shiny online certificate:

TL;DR Using short-lived secrets to access a database is much more secure than standard credentials
I recently received my AWS Solutions Architect Associate Cert, and I inadvertently learned more about Ops and DevOps in respect to automation, deployment an...
This post will cover the following: Connecting to Splunk with the Python SDK, executing a search and receiving the results Connecting to Splunk without ...
TL;DR: Create Logstash conf.d file to allow Winlogbeat to be ingested into Logstash. Change Winlogbeat config file to use Logstash instead of Elasticsearch.
TL;DR Enable-PSRemoting Invoke-Command
I have been working on Windows and needed to connect to a Network Interface (NIC). I ran into problems, here is what I learned and hope it saves the same tro...
I have been using tcpdump recently and wanted to note down some of the commands Y’know, for future reference.
Today I was trouble shooting a machine at work. I did not have access via RDP or VNC, so I used SSH to forward my traffic to the host so I could access a URL.
I participated in a DevSecOps type workshop on Saturday (May 9th) in which we created some GitHub Actions. This is a post to solidify the learning and be a c...
This post is a cheat sheet for removing values from a Slice (technically creating a new slice).
On April 25th I was fortunate enough to participate in the Trend Micro Threat Defense workshop.
Since I blogged about my experience at OpenSoc, I wanted to expand on the value I found in my eLearnSecuirty Incident Response course. What you will find bel...
So Thursday (April 9th) I participated in an online blue team defense simulation event, known as OpenSOC.
I have been working with Golang strings and how to manipulate them. Working from other blogs posts I’ve found. When I sit down to code, I seem to forget ever...
its workings
You’ll find this post in your _posts directory. Go ahead and edit it and re-build the site to see your changes. You can rebuild the site in many different wa...
Blog from home installed jekyll on home PC, pulled GH repo. done :) (not that easy)
2nd blog post this is some wording