Intro to Secrets Management using Vault
TL;DR Using short-lived secrets to access a database is much more secure than standard credentials
On April 25th I was fortunate enough to participate in the Trend Micro Threat Defense workshop.
You’ll find a quick explanation of this event and some screenshots.
At this workshop you will be working in teams with a scenario - a company is currently under attack. You are in charge of its protection. Live the adrenaline by defending the company from different attacks in real time whose objective is to steal the most important part of your business: Information. Be part of this experience and strengthen your security strategy, with the expert help. The aim is to win the Threat Defense Challenge, by gaining the most points through a series of discovery and attack challenges. Are you ready for the challenge?
The workshop had three phases based on hybrid data centre use cases:
The workshop was created by Trend Micro and organized in conjunction with the DC416 crew.

It was on a Saturday from 9am to 3:30pm. 6 and a half hours
The network was accessed via the cloud.
Systems within the game:
This was a Trend Micro event, meaning it was all designed and created by their team. As such the only tool given was Deep Security
Deep Security example:
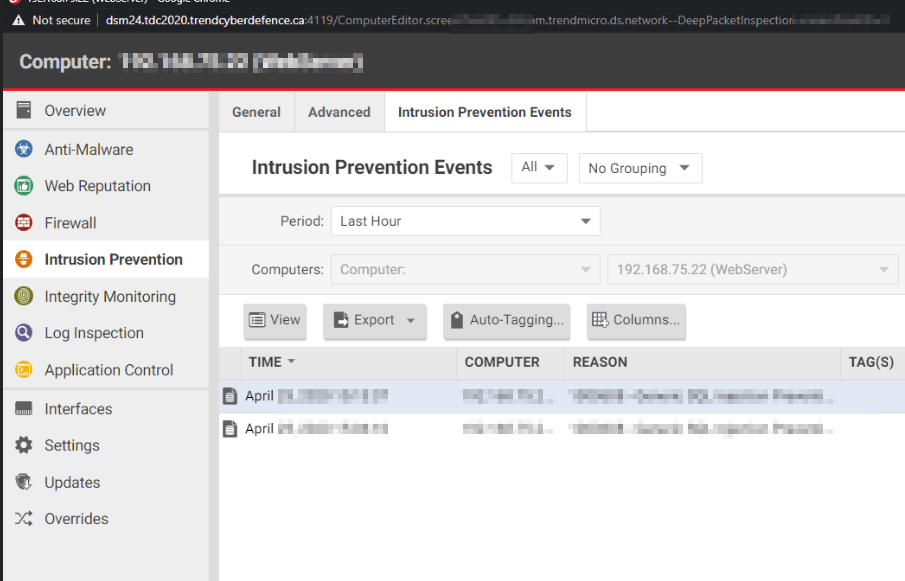
However there were other tools that were required:
We did not finish all the challenges, so there was much more to explore.
Varied from basic to hard.
Basic examples:
To more thinking outside the box:
Example finding malware:
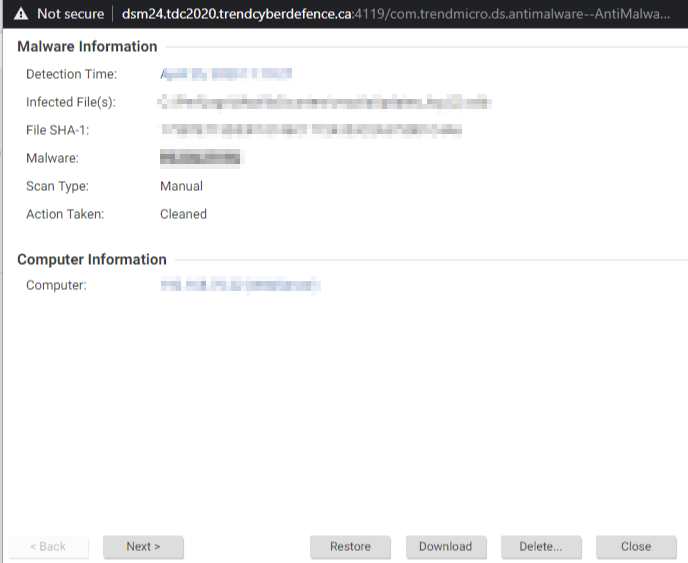
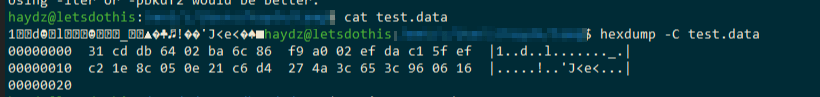
Example using hexdump, which was NOT the way to solve the challenge:
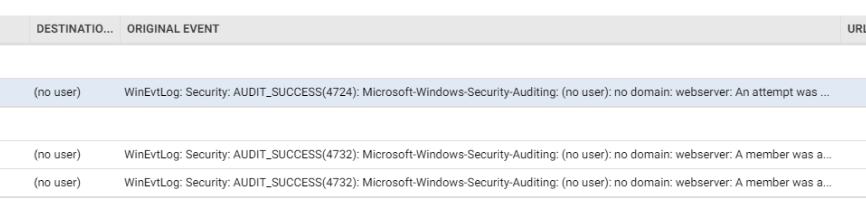
Example viewing Windows events through Deep Security:
This was a unique take on scoreboards.
Instead of just having a ladder and challenges. The idea was that you were ‘hacking around the world’. Each country had its own challenge. Obviously it started off in Canada!
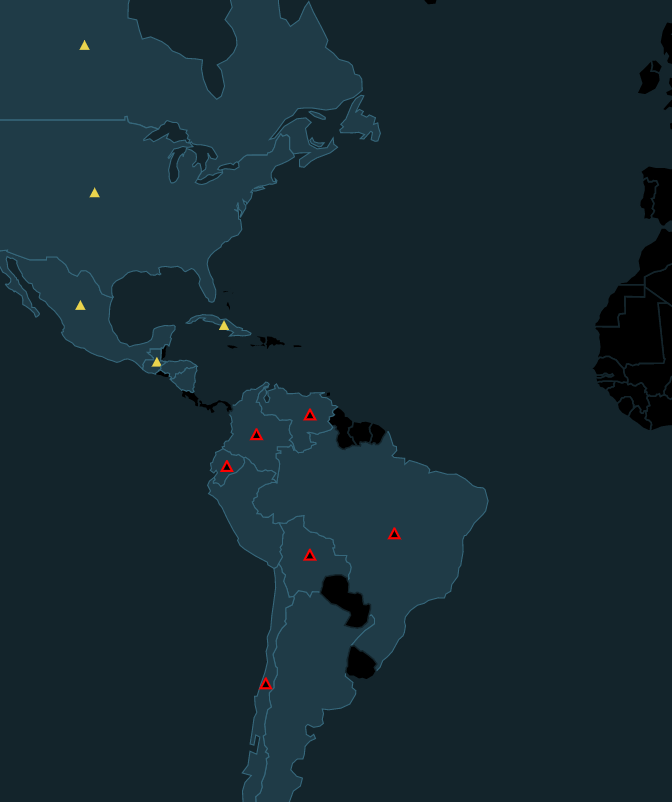
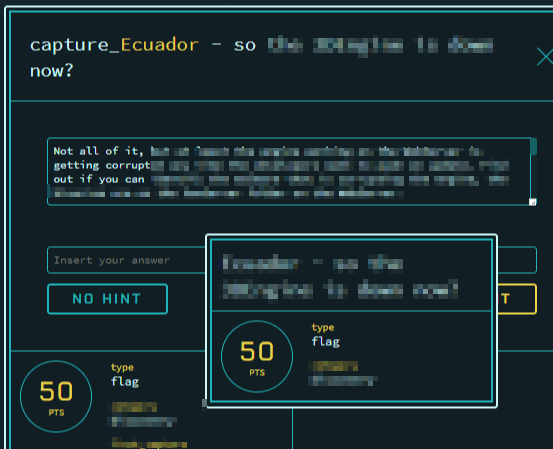
Example Challenges:
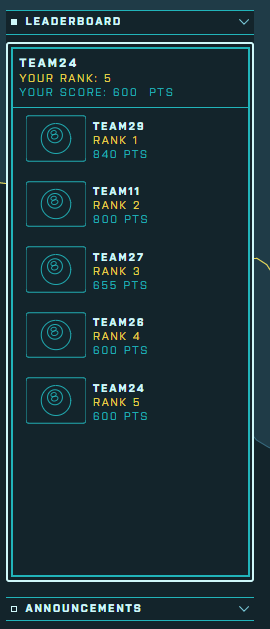
5th! Which I feel is pretty awesome. Also not bad for a team missing 1 team member. 3 members instead of 4 :D - Thanks Team mates! It was great to try a new tool and continue challenging myself.
TL;DR Using short-lived secrets to access a database is much more secure than standard credentials
I recently received my AWS Solutions Architect Associate Cert, and I inadvertently learned more about Ops and DevOps in respect to automation, deployment an...
This post will cover the following: Connecting to Splunk with the Python SDK, executing a search and receiving the results Connecting to Splunk without ...
TL;DR: Create Logstash conf.d file to allow Winlogbeat to be ingested into Logstash. Change Winlogbeat config file to use Logstash instead of Elasticsearch.
TL;DR Enable-PSRemoting Invoke-Command
I have been working on Windows and needed to connect to a Network Interface (NIC). I ran into problems, here is what I learned and hope it saves the same tro...
I have been using tcpdump recently and wanted to note down some of the commands Y’know, for future reference.
Today I was trouble shooting a machine at work. I did not have access via RDP or VNC, so I used SSH to forward my traffic to the host so I could access a URL.
I participated in a DevSecOps type workshop on Saturday (May 9th) in which we created some GitHub Actions. This is a post to solidify the learning and be a c...
This post is a cheat sheet for removing values from a Slice (technically creating a new slice).
On April 25th I was fortunate enough to participate in the Trend Micro Threat Defense workshop.
Since I blogged about my experience at OpenSoc, I wanted to expand on the value I found in my eLearnSecuirty Incident Response course. What you will find bel...
So Thursday (April 9th) I participated in an online blue team defense simulation event, known as OpenSOC.
I have been working with Golang strings and how to manipulate them. Working from other blogs posts I’ve found. When I sit down to code, I seem to forget ever...
its workings
You’ll find this post in your _posts directory. Go ahead and edit it and re-build the site to see your changes. You can rebuild the site in many different wa...
Blog from home installed jekyll on home PC, pulled GH repo. done :) (not that easy)
2nd blog post this is some wording