Intro to Secrets Management using Vault
TL;DR Using short-lived secrets to access a database is much more secure than standard credentials
Today I was trouble shooting a machine at work. I did not have access via RDP or VNC, so I used SSH to forward my traffic to the host so I could access a URL.
This is to serve as a cheat sheet for what I did, in case I need to do it again.
Side Note:
ssh -D 8080 user@192.x.x.x
This will dynamically forward any traffic through that host. Need to set a tool or browser for send traffic through local host on port 8080.
Key point: This will forward traffic through the host to any ip and port
Using Foxy Proxy:
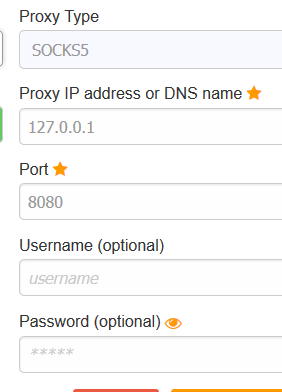
ssh -L 127.0.0.1:8080:192.168.1.1:80 hacker@192.168.1.2
This will forward local port 8080 traffic to 192.168.1.1 port 80 VIA (goes through 192.168.1.2)
ssh -L 127.0.0.1:8080:192.168.1.1:80 hacker@192.168.1.1
This will forward local port 8080 to the remote host and send the traffic to the remote hosts (192.168.1.1) port 80
TL;DR Using short-lived secrets to access a database is much more secure than standard credentials
I recently received my AWS Solutions Architect Associate Cert, and I inadvertently learned more about Ops and DevOps in respect to automation, deployment an...
This post will cover the following: Connecting to Splunk with the Python SDK, executing a search and receiving the results Connecting to Splunk without ...
TL;DR: Create Logstash conf.d file to allow Winlogbeat to be ingested into Logstash. Change Winlogbeat config file to use Logstash instead of Elasticsearch.
TL;DR Enable-PSRemoting Invoke-Command
I have been working on Windows and needed to connect to a Network Interface (NIC). I ran into problems, here is what I learned and hope it saves the same tro...
I have been using tcpdump recently and wanted to note down some of the commands Y’know, for future reference.
Today I was trouble shooting a machine at work. I did not have access via RDP or VNC, so I used SSH to forward my traffic to the host so I could access a URL.
I participated in a DevSecOps type workshop on Saturday (May 9th) in which we created some GitHub Actions. This is a post to solidify the learning and be a c...
This post is a cheat sheet for removing values from a Slice (technically creating a new slice).
On April 25th I was fortunate enough to participate in the Trend Micro Threat Defense workshop.
Since I blogged about my experience at OpenSoc, I wanted to expand on the value I found in my eLearnSecuirty Incident Response course. What you will find bel...
So Thursday (April 9th) I participated in an online blue team defense simulation event, known as OpenSOC.
I have been working with Golang strings and how to manipulate them. Working from other blogs posts I’ve found. When I sit down to code, I seem to forget ever...
its workings
You’ll find this post in your _posts directory. Go ahead and edit it and re-build the site to see your changes. You can rebuild the site in many different wa...
Blog from home installed jekyll on home PC, pulled GH repo. done :) (not that easy)
2nd blog post this is some wording