Intro to Secrets Management using Vault
TL;DR Using short-lived secrets to access a database is much more secure than standard credentials
Since I blogged about my experience at OpenSoc, I wanted to expand on the value I found in my eLearnSecuirty Incident Response course. What you will find below is a bit of a review of the course itself and the exam.
This post is not only intended to help others identify other training options, but also to serve as a refresher of the content I learned.
A review based on my specific circumstances and the value I gained from the certification.
eLearnSecurity is a serious alternative to other training providers that can cost up to 3 times more.
Full Transparency:
The course I signed up for was Incident Handling & Response Professional. It was released last year in January.
eLearnSecurity As you can see in the About Us section , eLearnSecurity is a training and certification company based in the US with offices still in Italy where the company was founded.

The security training space is very wide, both in cost and quality. You don’t always get what you pay for. I’m quite skeptical of training providers, associated costs and ‘certifications’ in general. I’m certainly not an expert. I use certifications as a guideline for my learning path, not the end all be all.
I work as a security manager looking after the overall program, in addition to analyst/pentest responsibilities. So the training I needed had to be applicable to my day job.
I don’t work at a company where security itself is a revenue generator, nor do I work at a company that is large. These 2 things mean I have a certain sized training budget that will not cover premium well known training providers.
So my criteria was the below:
I chose this training provider for the above reasons and after going through the course, I personally feel it met my 3 criteria superbly. This was mostly due to the fact that my day job for incident response is focused heavily in Splunk and the IHRP course covers this in-depth.
The course at a glance section:
Start from the very basics, all the way to advanced incident response activities
Professionally analyze, handle, and respond to security incidents on heterogeneous networks and assets
Understand the mechanics of modern cyber-attacks and how to detect them
Effectively use and fine-tune open source IDS (Bro, Snort, Suricata)
Make the best of open source SIEM solutions (ELK stack, Splunk, etc.)
Effectively utilize regexes and log management solutions to detect intrusions``
Detect and even (proactively) hunt for intrusions by analyzing traffic, flows and endpoints, as well as utilizing analytics and tactical threat intelligence
Gives you access to dedicated forums
Makes you a proficient professional incident responder
After obtaining the eCIRv1 certification qualifies you for 40 CPE
First off, the interest will probably be with the “What is the certification exam like” or “what do I get out of the exam”.
I have completed a practical hands on exam in offensive security and a multiple choice exam for offensive security. I learned, applied and retained much more in a practical exam setting.
The exam is all hands-on. There are zero multiple choice questions. It is a scenario based (2) exam. Requiring not just technical knowledge of Splunk and ELK but understanding the business and critical assets in order to inform your investigative process. There is a component of network traffic analysis to mix it up and give another way to gain visibility on the attack.
The practical portion is 2 full days.
There is also an additional 2 days for report writing. That is, take all the notes from the practical portion and report on the what the attacker ‘did’. That could be anything from the Cyber Kill Chain, such as initial infection, moving to different systems, persistence and or something related to “acting on objectives”.
More can be read Here
Investigation is contextual, based on critical assets, initial infection and the network etc.
The exam is difficult in that identifying each technique used and each stage on the kill chain is not a point and click exercise, nor is it to the extreme difficulty requiring years of experience in the field.
The exam for me seemed balanced between requiring most of the investigation techniques taught in the course, and requiring use of the “process of investigation” taught in the course. By process of investigation I mean following the indicators that you have found, instead of copy pasting pre-made queries (like my cheat sheet). In saying that, it did push me and my skills up a notch.
The exam also requires friendly intelligence, such as understanding which host is owned by which user etc. (skills that pentesters use as well).
Side note: The sources in the exam platforms are not the same as in the lab. So copy and paste will not work.
What you get out of the exam
For all intents and purposes, the course teaches you what you need know to pass the exam.
However in saying that, if all you do is the course the exam might be much more difficult than need be.
It is a good idea to spend extra time in the platforms either by building your own home lab or finding something online. Try to become more ‘fluent’ and comfortable with Splunk and ELK. During the exam you will feel the pressure and you don’t want to be googling basic syntax command prior to considering what to look for.
Another thing I found that helped, was reading on the same topics outside of the course. This helped understand other ways tools could be used, other thought processes for investigation.
The tools covered include:
Incident Response Platforms
IDS/IPS:
SIEM Platforms:
The labs do a fine job of getting you acquainted with the tools and providing varying levels of depth. Sometimes going beyond the tool.
For transparency:
These were good just to be able to understand the benefits of having a centralized platform for IR, including being able to pull information such as a list of files in a suspect directory.
I did not have to set these up myself, the labs had it all installed.
This is NOT an exhaustive description, but the most valuable knowledge I gained.
By flowing, I mean the opposite of staring at a search bar in Splunk or ELK and going ‘where do I even start’. The ability to change queries to get different information as needed.
Unfortunately there is a load of theory to cover to be able to do this. I’ve since found I am able to look through different logs and sources within the 2 platforms much more efficiently. I still have to google things now and again for exact syntax or something, but in general I ‘understand’ possible locations for where information related to an incident could be.
There is never a straight forward investigation to an attack. There is no answer like “machine dropped malware then moved to machine B”. Especially when there is legitimate traffic flowing around.
I have many notes now on ELK and Splunk queries to help me jump start an investigation.
As an example I have notes on LM/NTML
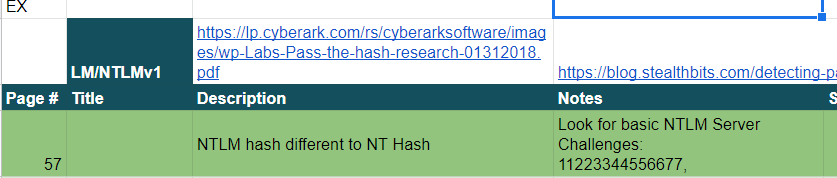
A Splunk search for privileges that can be abused:
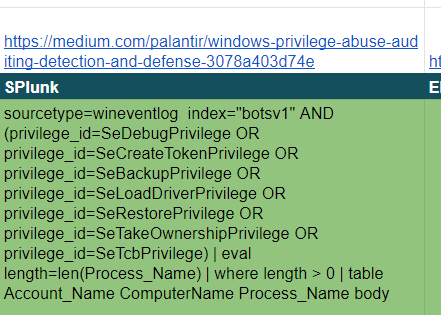
I imagine it would be beneficial if I went for a job related to a SOC or for an IR position to be to say I have a cheatsheet. A playbook to guide to my investigations. This would show that even though I may not do IR every day, I think about what I am doing, what works and what does not, instead of starting from scratch each time.
The benefit for me, is that it keeps my options open. I am still fine tuning my career and want to be able to change career paths if needed.
Not having to rely on one tool will be beneficial. Especially if consulting at different clients.
The value I found in here, was being able to evaluate the pros and cons of the tools. Such as skill required, effort to maintain or tune and or cost of deployment (purchase price, time & effort).
Obviously at a company, we use an IDS/IPS and it was beneficial to be able to make sure that at my job we could get the most out of the platform, such as tuning it a bit better or understanding its limitations better.
Because it is not my day to day role, I wrote a blog post based on some of the learning on zeek here. it is very short but will help me quickly be able to read a PCAP and or write a rule if needed. - It is also on my old blog site (horrible and ugly to edit and look at).
I have a Suricata Cheat Sheet post as well. It includes basic references for writing rules. Find it here
Example:
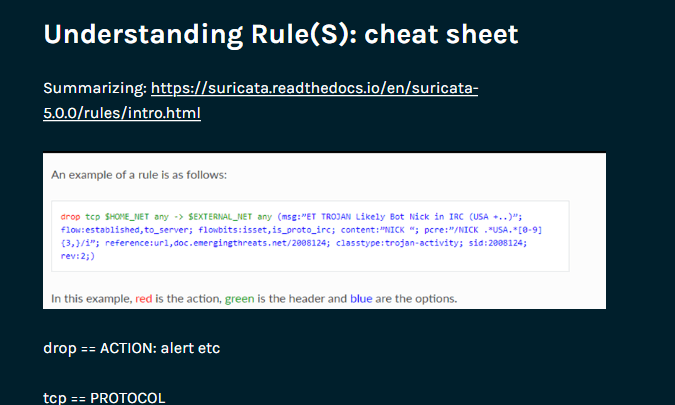
For someone junior, being exposed to the tools and having a go at writing your own rules would be invaluable.
For someone like myself, the value is not only in being able to run the tool and tune rules, but also understanding how it gets deployed, the effort to maintain it, and where the sensors should be. How to justify the value of the tool (via understanding what it does and what it does not do) to upper management is also a plus.
My initial experience and interest within infosec was penetration testing. I would research online how to fix or defend against the techniques used. But I hadn’t experienced it from a true Enterprise defender side before. Sure I had installed Splunk and a home lab, but it isn’t the same.
Attacks look very different from the defender side, with a lot of friendly traffic attacks are difficult to detect. Add in false-positives and the difficulty raises even further.
The value for me, is the high level actions that can be taken and how those filter down into a log or combination of logs.
For example, in an active directory environment, the Domain Controllers hold some logs and the clients hold other logs, requiring both to put the full piece together. Or in case of the exam, comparing logs with network traffic analysis.
Not so much of importance for myself. However:
The courses such as this one are design around the NIST NICE Cybersecurity Workforce framework
From their website
The NICE Framework, NIST Special Publication 800-181, is a national-focused resource that categorizes and describes cybersecurity work.
and
Current and future cybersecurity workers, to help explore Tasks and Work Roles and assist with understanding the KSAs that are being valued by employers for in-demand cybersecurity jobs and positions.
IHRP/eCIR is developed towards the following NIST roles:
Upon looking at the PDF, the description of Cyber Incident Responder and Cyber Defense Incident Response appear to match with the content of the course.


There is a lot of theory. Theory is extremely important to learn and can be overwhelming. Try to drink from the fire hose and you will burn out. I see this as a necessary evil due to the complexities of what attackers can do on a machine, on both Linux and Windows.
Reading standard text is never fun, but critical. For example, if you don’t know which windows event log and login type shows a remote login, how will you know to search for it in Splunk? The answer is 4624 with a logon type 3 for Network.
Which is part of the cheat sheets I created:
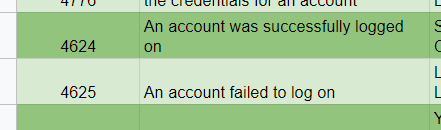
For transparency: Yes there are some grammatical errors. The author is from Greece originally so it is understandable. His expertise is within IR not English.
TL;DR Using short-lived secrets to access a database is much more secure than standard credentials
I recently received my AWS Solutions Architect Associate Cert, and I inadvertently learned more about Ops and DevOps in respect to automation, deployment an...
This post will cover the following: Connecting to Splunk with the Python SDK, executing a search and receiving the results Connecting to Splunk without ...
TL;DR: Create Logstash conf.d file to allow Winlogbeat to be ingested into Logstash. Change Winlogbeat config file to use Logstash instead of Elasticsearch.
TL;DR Enable-PSRemoting Invoke-Command
I have been working on Windows and needed to connect to a Network Interface (NIC). I ran into problems, here is what I learned and hope it saves the same tro...
I have been using tcpdump recently and wanted to note down some of the commands Y’know, for future reference.
Today I was trouble shooting a machine at work. I did not have access via RDP or VNC, so I used SSH to forward my traffic to the host so I could access a URL.
I participated in a DevSecOps type workshop on Saturday (May 9th) in which we created some GitHub Actions. This is a post to solidify the learning and be a c...
This post is a cheat sheet for removing values from a Slice (technically creating a new slice).
On April 25th I was fortunate enough to participate in the Trend Micro Threat Defense workshop.
Since I blogged about my experience at OpenSoc, I wanted to expand on the value I found in my eLearnSecuirty Incident Response course. What you will find bel...
So Thursday (April 9th) I participated in an online blue team defense simulation event, known as OpenSOC.
I have been working with Golang strings and how to manipulate them. Working from other blogs posts I’ve found. When I sit down to code, I seem to forget ever...
its workings
You’ll find this post in your _posts directory. Go ahead and edit it and re-build the site to see your changes. You can rebuild the site in many different wa...
Blog from home installed jekyll on home PC, pulled GH repo. done :) (not that easy)
2nd blog post this is some wording