Intro to Secrets Management using Vault
TL;DR Using short-lived secrets to access a database is much more secure than standard credentials
TL;DR: Create Logstash conf.d file to allow Winlogbeat to be ingested into Logstash. Change Winlogbeat config file to use Logstash instead of Elasticsearch.
I had trouble installing ELK and configuring it to accept Winlogbeat, I went down a rabbit hole attempting to use Elasticsearch. This is an explanation of how to do it correctly without ELK being forced into ‘production mode’.
Production mode meaning: All warnings become errors and if they are not resolved, Elasticsearch will not launch.
It is assumed that an instance of ELK has been installed and is up and running.
Follow the install guide from elastic.co here
ELK should look like this, it does not need to be ingesting any logs.
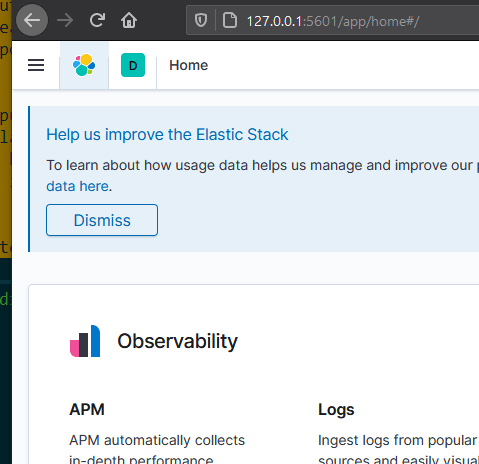
Winglogbeat should also be installed, the install guide can be found here.
ONLY FOLLOW STEP 1: INSTALL WINLOGBEAT
The Quick start install and configuration guide from Step 2 will use ElasticSearch, and that is not the configuration used in this post.
Not the only way, but the way that allows ingesting Winlogbeat without having to go into production mode.
The way to do this is to use Logstash.
In short:
If you read about how Logstash works, it has a processing pipeline of inputs, filters and outputs.
First off: A configuration file that has an input, filter (optional) and output is called a Pipeline configuration file.
Pipeline configuration files go in the /etc/Logstash/conf.d/ directory. Explained here
The full path in a Linux installation is:
/etc/Logstash/conf.d$
Structure of a Config File explanation
Configuration examples if needed can be found here
Inputs generate events, filters modify them, and outputs ship them elsewhere. Inputs and outputs support codecs that enable you to encode or decode the data as it enters or exits the pipeline without having to use a separate filter.
This paragraph means the steps required are:
If you are new to ELK it can be quite a bit of a jump to ingesting Winlogbeat into Logstash instead of ElasticSearch.
The important thing to understand is that Winlogbeat is a type of ‘Beats’ and Logstash works well with them thanks to a Beat input plugin. There are many types of ‘Beats’, all of them are listed here
Beats can be thought of like a ready to go log forwarder that sit on the endpoint you want to receive logs from. In the case of Winlogbeat it will sit on a Windows machine and send the logs to Logstash.
Following along the Beats Input Plugin Page there is a basic configuration file that ingests beats. The configuration file follows the Pipeline Configuration format mentioned above.
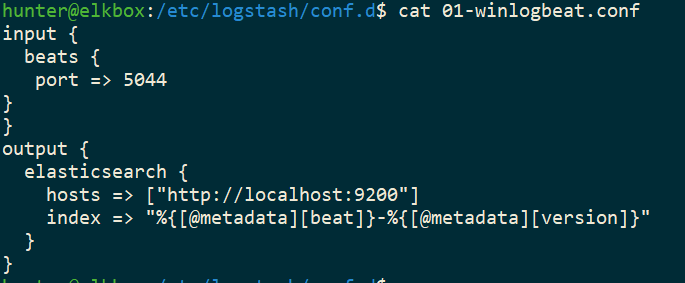
input {
beats {
port => 5044
}
}
output {
elasticsearch {
hosts => ["http://localhost:9200"]
index => "%{[@metadata][beat]}-%{[@metadata][version]}"
}
}
This is used to tell Logstash to listen/ingest incoming Beats connections and to index them into Elasticsearch.
Save this file with the extension .conf within the conf.d directory. The full directory path should be:
/etc/Logstash/conf.d
Like this:
Stop and Start Logstash, perhaps even Elasticsearch to ensure the new configuration is being used.
Logstash is now setup to ingest beats, including Winlogbeat. The next step is to configure Winlogbeat to use Logstash instead of Elasticsearch.
The YAML file will be edited to send the Winlogbeat logs to Logstash.
After following the default installation (mentioned in the Prerequisite section) Winlogbeat should be installed here:
C:\Program Files\Winlogbeat
The configuration file is called:
winlogbeat.yml
Edit the file and comment out (add the ‘#’ in front) of the Elasticsearch settings, these can be found in the Elasticsearch Output section:
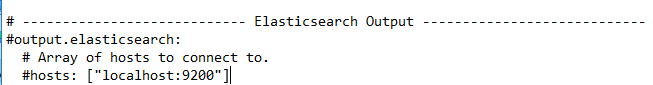
The complete Elasticsearch Option Section will look like:
# ---------------------------- Elasticsearch Output ----------------------------
#output.elasticsearch:
# Array of hosts to connect to.
#hosts: ["localhost:9200"]
# Protocol - either `http` (default) or `https`.
#protocol: "https"
# Authentication credentials - either API key or username/password.
#api_key: "id:api_key"
#username: "elastic"
#password: "changeme"
Scroll down to the Logstash Output section and uncomment (remove the ‘#’) settings. Be sure to change localhost with the IP address of the ELK box.
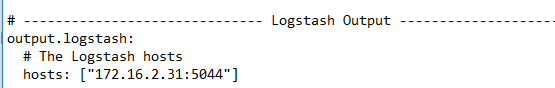
The complete Logstash Output Section will look like:
# ------------------------------ Logstash Output -------------------------------
output.Logstash:
# The Logstash hosts
hosts: ["172.16.2.31:5044"]
# Optional SSL. By default is off.
# List of root certificates for HTTPS server verifications
#ssl.certificate_authorities: ["/etc/pki/root/ca.pem"]
# Certificate for SSL client authentication
#ssl.certificate: "/etc/pki/client/cert.pem"
# Client Certificate Key
#ssl.key: "/etc/pki/client/cert.key"
Stop and Start Winlogbeat to ensure the new configuration is being used.
With Logstash and Winlogbeat configured correctly, Kibana should have an index pattern of winlogbeat-
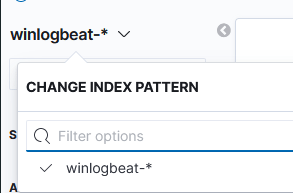
Please follow the Define your index patterns guide and use “winlogbeat-*”.
Elasticsearch by default only accepts data from localhost. If the network.host line in the YAML file is configured to an external address it will go into ‘Production Mode’:
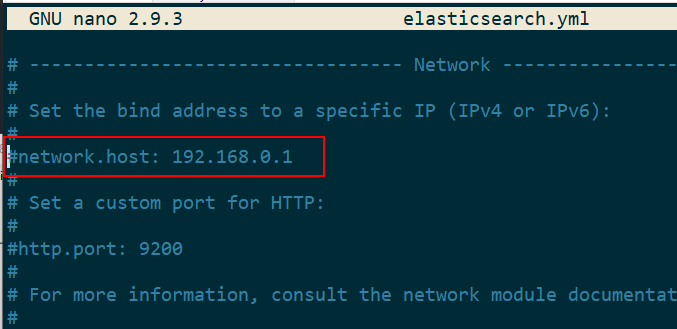
If Elasticsearch is started without fixing all ‘warnings’ it will not start and give the following error:

Viewing the logs does not give an indication of Production Mode.
However looking at the Important System Configuration Documentation there is a line such as “As soon as you configure a network setting like network.host, Elasticsearch assumes that you are moving to production and will upgrade the above warnings to exceptions. These exceptions will prevent your Elasticsearch node from starting. This is an important safety measure to ensure that you will not lose data because of a malconfigured server.”
Thus, if installing Elasticsearch as described in the Quick start and installation guide non-production systems will run into this issue.
All the settings that need to be considered include:
TL;DR Using short-lived secrets to access a database is much more secure than standard credentials
I recently received my AWS Solutions Architect Associate Cert, and I inadvertently learned more about Ops and DevOps in respect to automation, deployment an...
This post will cover the following: Connecting to Splunk with the Python SDK, executing a search and receiving the results Connecting to Splunk without ...
TL;DR: Create Logstash conf.d file to allow Winlogbeat to be ingested into Logstash. Change Winlogbeat config file to use Logstash instead of Elasticsearch.
TL;DR Enable-PSRemoting Invoke-Command
I have been working on Windows and needed to connect to a Network Interface (NIC). I ran into problems, here is what I learned and hope it saves the same tro...
I have been using tcpdump recently and wanted to note down some of the commands Y’know, for future reference.
Today I was trouble shooting a machine at work. I did not have access via RDP or VNC, so I used SSH to forward my traffic to the host so I could access a URL.
I participated in a DevSecOps type workshop on Saturday (May 9th) in which we created some GitHub Actions. This is a post to solidify the learning and be a c...
This post is a cheat sheet for removing values from a Slice (technically creating a new slice).
On April 25th I was fortunate enough to participate in the Trend Micro Threat Defense workshop.
Since I blogged about my experience at OpenSoc, I wanted to expand on the value I found in my eLearnSecuirty Incident Response course. What you will find bel...
So Thursday (April 9th) I participated in an online blue team defense simulation event, known as OpenSOC.
I have been working with Golang strings and how to manipulate them. Working from other blogs posts I’ve found. When I sit down to code, I seem to forget ever...
its workings
You’ll find this post in your _posts directory. Go ahead and edit it and re-build the site to see your changes. You can rebuild the site in many different wa...
Blog from home installed jekyll on home PC, pulled GH repo. done :) (not that easy)
2nd blog post this is some wording