Intro to Secrets Management using Vault
TL;DR Using short-lived secrets to access a database is much more secure than standard credentials
I participated in a DevSecOps type workshop on Saturday (May 9th) in which we created some GitHub Actions. This is a post to solidify the learning and be a cheat sheet.
Again DC416 hosted an online workshop. It was run by Tanya.
It was titled “DC416 DevSecOps Workshop with GitHub Actions and Azure”.
I learned a bit and had fun.
Add a pipeline to our process to deploy code from GitHub to a web-app on Azure and use various security tooling within the pipeline
It was pretty cool.
Anyhow. To the Cheat sheet on GitHub actions.
GitHub Actions makes it easy to automate all your software workflows, now with world-class CI/CD. Build, test, and deploy your code right from GitHub. Make code reviews, branch management, and issue triaging work the way you want.
For me, this means that any time I commit code I can have it check that my work email is not in my code. Why my email? Because if I have my work email hard-coded in a script, it probably means I have my work password hard-coded as well. Which is…. really bad
The first tutorial I followed was Hello World
There are many GitHub Actions people have created. You can find them on the marketplace.
Search for them like so:

So a GitHub action actually ties into a workflow.
Custom workflows are automatic processes that are setup in a GitHub repo. So you would have a workflow that executes a GitHub Action.
From the documentation
Workflows must have at least one job, and jobs contain a set of steps that perform individual tasks. Steps can run commands or use an action. You can create your own actions or use actions shared by the GitHub community and customize them as needed.
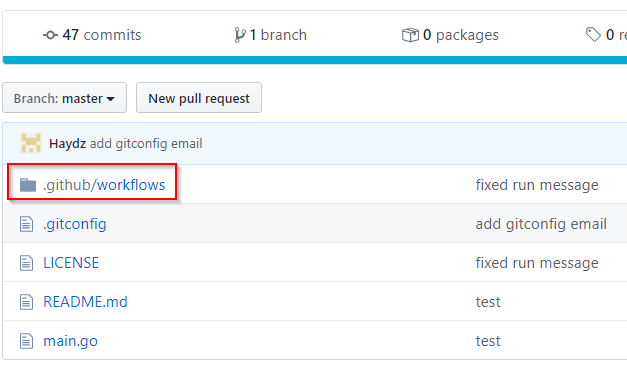
.github/workflowsNote: in #2 the example will be to execute a search for the work email (Trufflehog) on a commit/push to GitHub.
Simply create the directory within the GitHub Repo:
.github/workflows
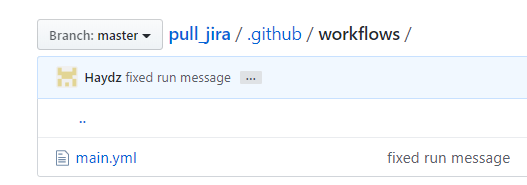
The .yml file needs to be created within the workflows directory.
Again, in the documentation there is an example workflow file.
name: Greet Everyone
# This workflow is triggered on pushes to the repository.
on: [push]
jobs:
build:
# Job name is Greeting
name: Greeting
# This job runs on Linux
runs-on: ubuntu-latest
steps:
# This step uses GitHub's hello-world-javascript-action: https://github.com/actions/hello-world-javascript-action
- name: Hello world
uses: actions/hello-world-javascript-action@v1
with:
who-to-greet: 'Mona the Octocat'
id: hello
# This step prints an output (time) from the previous step's action.
- name: Echo the greeting's time
run: echo 'The time was $.'
The example shows:
We will come back to this after we find the TruffleHog GitHub action.
Looking for TruffleHog I found 2 types. One is based off the original but does not allow configuration changes.
For this example we will use Trufflehog Actions Scan
This GitHub action allows basic configuration
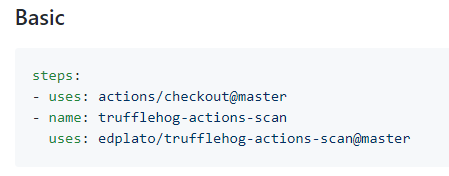
As well as custom configuration.
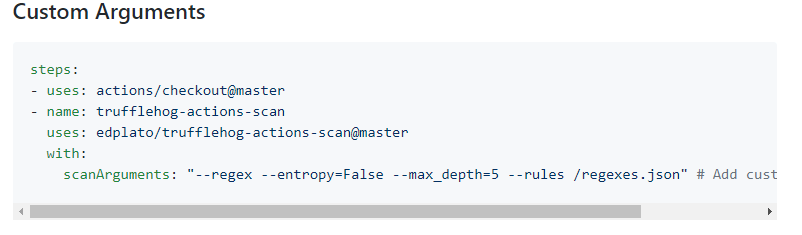
Within the custom Arguments configuration, we can see the --rules line with a regexes.json file. - This will be the file we edit to add a custom rule to look for a work email.
Here we can add TruffleHog as it is without customization. To do this, follow the below:
Back to the GitHub repo where the yaml file was created. We need to add a job to execute the GitHub action.
The link for my YAML file location is: https://github.com/Haydz/jirapull/blob/master/.github/workflows/main.yml
Edit your YAML file to like so:
name: A workflow for ensuring credentials are not in file
on: push
jobs:
build:
name: Cred Checker
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@master
- name: trufflehog-actions-scan
uses: edplato/trufflehog-actions-scan
The above file takes the following parts from the example workflow file and the Trufflehog documentation:
If this is commited in GitHub, it should start off the Trufflehog GitHub Action.
You can look in the actions section:
https://github.com/Haydz/jirapull/actions
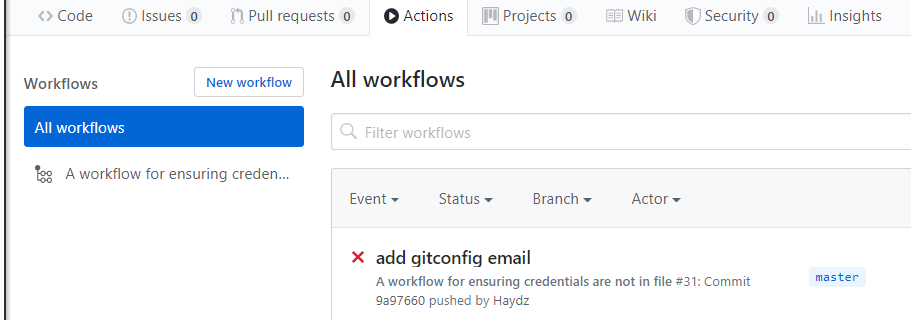
If you click into it, it will look something like the following, but will most likely pass as your code probably does not have any secrets in it:
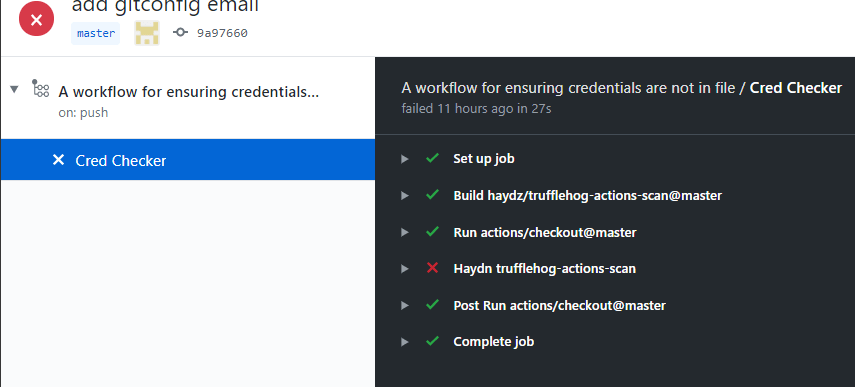
So this is an example of having Trufflehog running.
The steps to customize Trufflehog to look for an email address are below:
Just like any GitHub repo that requires customization, forking the repo is needed.
Find the repo by clicking on use latest version:
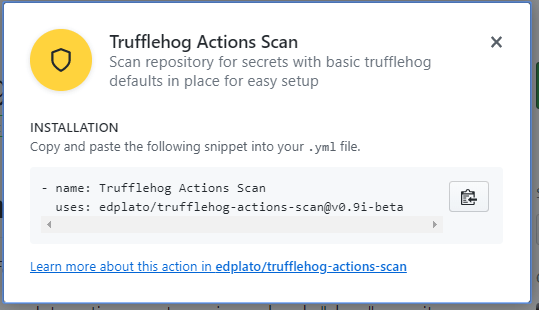
Then clicking the learn more here link. Which takes us to the correct repo.
To be able to edit it, we need to fork it:
My URL location ends up being the following, yours will be similar but with your GitHub username. https://github.com/Haydz/trufflehog-actions-scan
There was a rules file listed in the instructions. So its best to look at that.
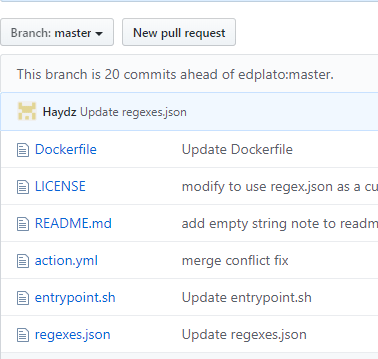
In short, it is a list of regex rules that will the action will alert on:
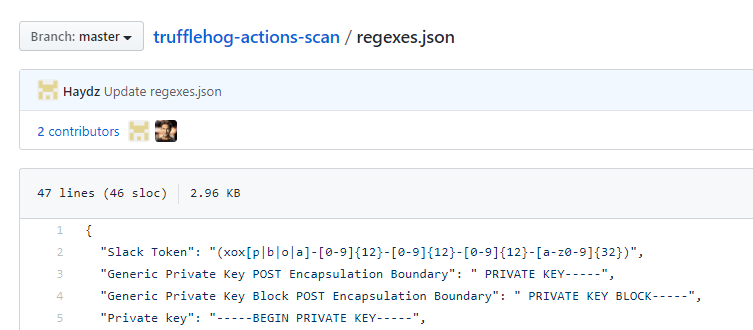
Edit this with your work email, or a secret you want to find.
My example is anything with a name.lastname@fakemail.com format:
` “Work email”: “\w\.\w@fakemail\.com”`
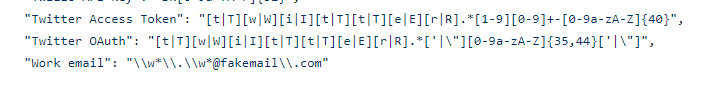
This will allow Trufflehog to use the rules list and search based on the regex.
Editing the forked versions regex rules is great. But if the YAML is configured correctly, it will still run the Trufflehog version found at “edplato/trufflehog-actions-scan”
So the YAML file should be edited for the forked version like so:
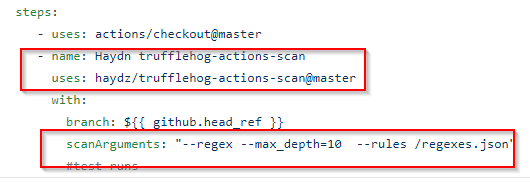
Focusing on:
The complete file will look like:
name: A workflow for ensuring credentials are not in file
on: push
jobs:
build:
name: Cred Checker
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@master
- name: Haydn trufflehog-actions-scan
uses: haydz/trufflehog-actions-scan@master
with:
scanArguments: "--regex --max_depth=10 --rules /regexes.json"
My Yaml can be found here
So it appears everything is in order.
We should create a file with the email address in it, and commit the file to test if the regex is working correctly.
The example here is a file called testemail with the contents:
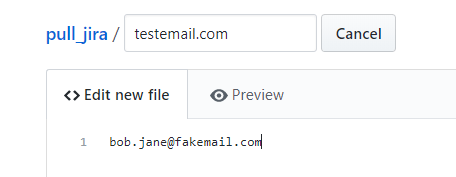
Once this is commited, the Github Action will run.
Commit the file:
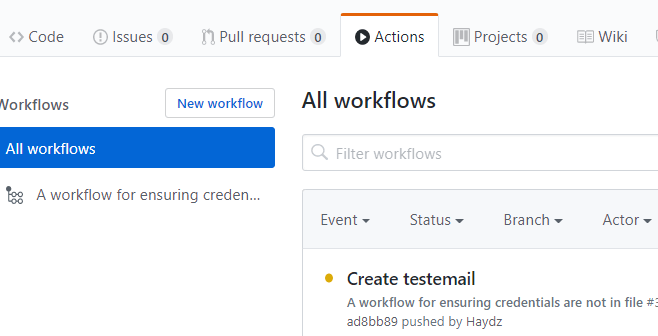
Then go to the Actions Section, and it should be running:
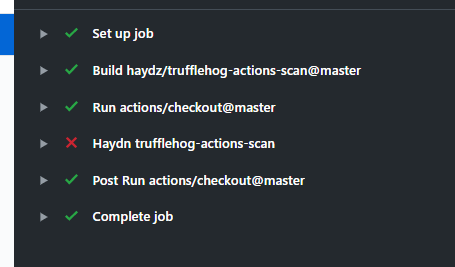
It runs and errors:
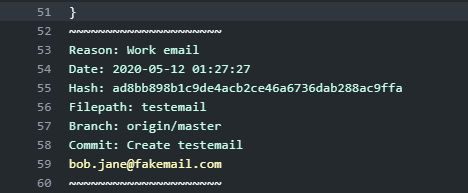
Looking within the Trufflehog scan results, it successfully detected the email address:
Success!
TL;DR Using short-lived secrets to access a database is much more secure than standard credentials
I recently received my AWS Solutions Architect Associate Cert, and I inadvertently learned more about Ops and DevOps in respect to automation, deployment an...
This post will cover the following: Connecting to Splunk with the Python SDK, executing a search and receiving the results Connecting to Splunk without ...
TL;DR: Create Logstash conf.d file to allow Winlogbeat to be ingested into Logstash. Change Winlogbeat config file to use Logstash instead of Elasticsearch.
TL;DR Enable-PSRemoting Invoke-Command
I have been working on Windows and needed to connect to a Network Interface (NIC). I ran into problems, here is what I learned and hope it saves the same tro...
I have been using tcpdump recently and wanted to note down some of the commands Y’know, for future reference.
Today I was trouble shooting a machine at work. I did not have access via RDP or VNC, so I used SSH to forward my traffic to the host so I could access a URL.
I participated in a DevSecOps type workshop on Saturday (May 9th) in which we created some GitHub Actions. This is a post to solidify the learning and be a c...
This post is a cheat sheet for removing values from a Slice (technically creating a new slice).
On April 25th I was fortunate enough to participate in the Trend Micro Threat Defense workshop.
Since I blogged about my experience at OpenSoc, I wanted to expand on the value I found in my eLearnSecuirty Incident Response course. What you will find bel...
So Thursday (April 9th) I participated in an online blue team defense simulation event, known as OpenSOC.
I have been working with Golang strings and how to manipulate them. Working from other blogs posts I’ve found. When I sit down to code, I seem to forget ever...
its workings
You’ll find this post in your _posts directory. Go ahead and edit it and re-build the site to see your changes. You can rebuild the site in many different wa...
Blog from home installed jekyll on home PC, pulled GH repo. done :) (not that easy)
2nd blog post this is some wording